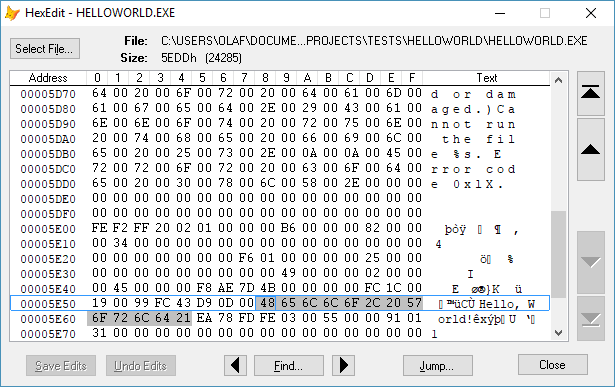
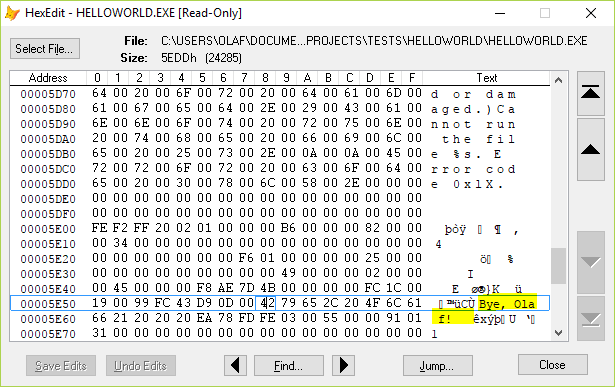
A protection even of a simple text file is possible by cryptographically signing it.
What this means is not write protecting the file, but enabling to detect any changes made to it.
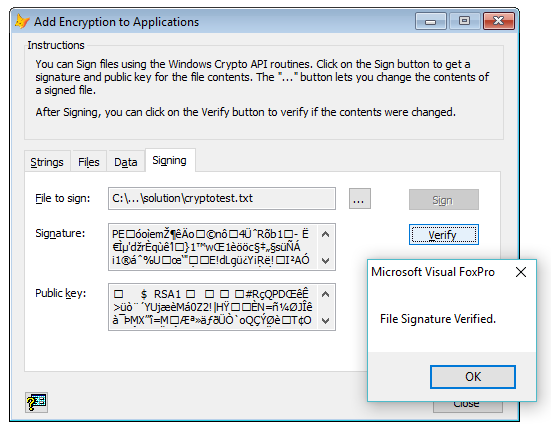
VFP has the _crpty.vcx in ffc with the _cryptapi class, this has the methods signfile() and verifyfilesginature().
The solution sample "Add encryption to applications" within the "Foundation Classes" section of the solution sample shows how to make use of these methods:
What you do is sign a file you want to verify being unchanged, then store both the signature and public key separate, this time putting it within your code would be fine. Even if someone would identify which bytes of your final EXE store this signature and public key, changing both would be required because the signature can only be created with a private key, which is not output here and also shouldn't ever be output, as it's your secret. It's autogenerated by the _cryptapi class. And generating a new signature with a new key pair requires to both change signature and public key to be able to pass that verification test again.
Now at the start of your application, you verify the file signature and if it's invalid simply quit. This still enables to run a copy and as Mike said nobody would be discouraged by a message or splash screen showing someone else's name, so it's quite useless as protection, unless you can store and sign something, which is necessary to run and would need to be changed on another computer, like serial numbers. The problem with that is you don't know in advance what the CPU hard drive or other serial numbers of your customer are, so you'd need to provide the signing procedure and your private key, which you never should distribute. Instead, there would be a process at installation or the first start transferring such information to you, so you can sign it at your computer and return back the file generated from this information and its signature.
This still is quite unsatisfactory in the process for your customers. Also, I faintly remember one of the signature standards was broken and since VFP9 is over ten years old it's likely you better use something more modern for secure encryption including signing data.
So for real protection I'd always go for an expert on this, and though I know about that _crypt.vcx and have implemented encryption and signing in a POS system this year, this used a library from a vendor trusted by austrian government and not something from VFP FFC, so such things are better not written yourself, even not on the highest level of using well-known cryptography algorithms, as an insecure usage of highly secure algorithms still is insecure overall. In this case, the autogeneration of keys remains some secret, I don't see how to use _crytpapi methods to retrieve the private key to store it for repeatably signing information with the same key pair, for example. While you should never distribute it, you should be able to maintain it for yourself. That also opens other possibilities, eg decryption of messages sent from your application to you encrypted with the known public key. You'll need to know your private key for decryption, though.
Overall, there are commercial products for software protection and they exist for a good reason. You should use something from a third party, from a vendor which is expert on that field.
Bye, Olaf.