thread690-1803251
kyle555 (TechnicalUser)15 Jun 20 15:44
Didn't have time to answer yesterday.
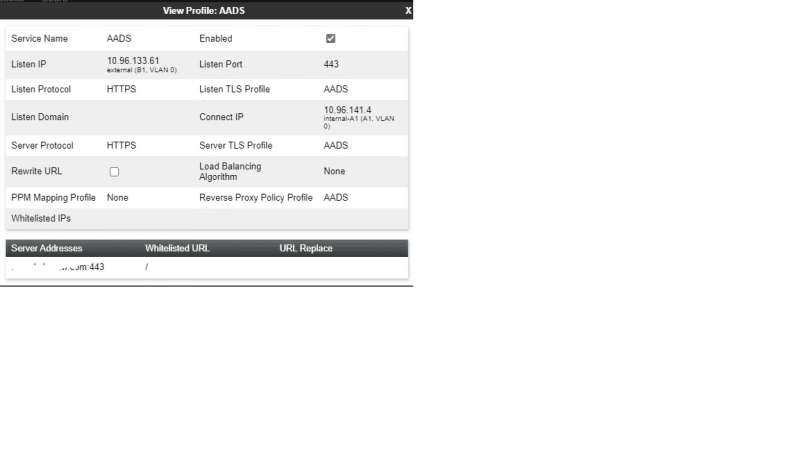
When you're logged in and type a name to search, AADS uses the Bind DN as the account it logs into LDAP with to make the search.
That has nothing to do with getting users authenticated.
AADS supports many different roles - only the Users are the ones that use IX Workplace. Service Admin, Auditor, etc are roles that are for specific tasks. So, if you want someone to be able to restart AADS but not make config changes, you'd make them a Service Admin.
So, those role fields are groups or folders in LDAP. So, if mohamed@lab.com with DN=mohamed,CN=users,dc=lab,dc=com logs in to IX Workplace and the user role = CN=users,dc=lab,dc=com, then you'll be allowed to login and AADS will try to match your userPrincipalName to a SMGRLogin name in the attribute mappings and associate your LDAP account with your Avaya account.
Now, lets say you have a group CN=AADSAdmins,CN=users,dc=lab,dc=com and mohamed is a member of that group and if I did a ldap search for members of CN=AADSAdmins,CN=users,dc=lab,dc=com and you showed up, then if you went to in your browser and logged in as mohamed, you'd be allowed to login as an admin.
Does that means to get the users authenticated through AADS (finally AD), the users should be added to the AADSUser group ?
kyle555 (TechnicalUser)15 Jun 20 15:44
Didn't have time to answer yesterday.
When you're logged in and type a name to search, AADS uses the Bind DN as the account it logs into LDAP with to make the search.
That has nothing to do with getting users authenticated.
AADS supports many different roles - only the Users are the ones that use IX Workplace. Service Admin, Auditor, etc are roles that are for specific tasks. So, if you want someone to be able to restart AADS but not make config changes, you'd make them a Service Admin.
So, those role fields are groups or folders in LDAP. So, if mohamed@lab.com with DN=mohamed,CN=users,dc=lab,dc=com logs in to IX Workplace and the user role = CN=users,dc=lab,dc=com, then you'll be allowed to login and AADS will try to match your userPrincipalName to a SMGRLogin name in the attribute mappings and associate your LDAP account with your Avaya account.
Now, lets say you have a group CN=AADSAdmins,CN=users,dc=lab,dc=com and mohamed is a member of that group and if I did a ldap search for members of CN=AADSAdmins,CN=users,dc=lab,dc=com and you showed up, then if you went to in your browser and logged in as mohamed, you'd be allowed to login as an admin.
Does that means to get the users authenticated through AADS (finally AD), the users should be added to the AADSUser group ?