Just to demonstrate the ineffectiveness of the EXE encryption VFP offers.
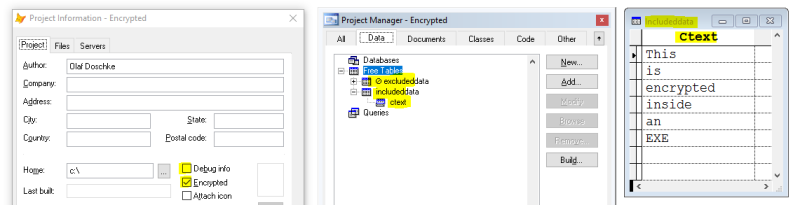
Here's a project with a DBF I include in the EXE:
Notice the project info has checked "Encrypted", no debug info (sources) are included, the includeddata.dbf is included in the built EXE, the excludeddata.dbf has a small icon crossed circle, which is default excluded status for any DBFs you put into PJXes, so includeddata is explicitly included. The data inside the includeddata.dbf is shown on the right.
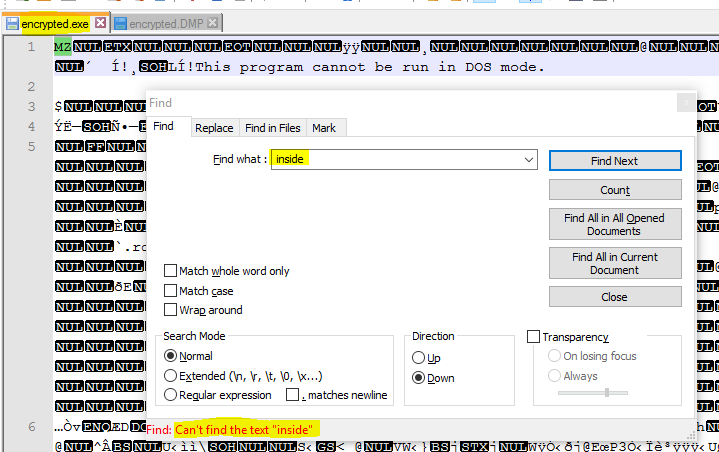
Here I now inspect the built EXE about it's encryption. I make a simple test, whether the words of the DBF cannot be found and notepad++ here states it cannot find the word "inside", which is one of the words in the data. This is proof the embedded data is not in clear text.
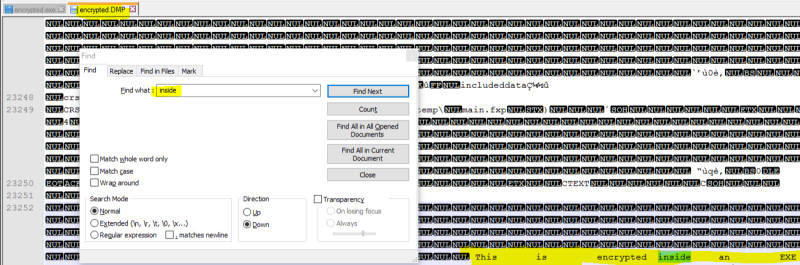
Now I started the EXE and used task manager to make a dump file of memory contents related to this EXE and loaded DLLs.
This shows up as this DMP file and notepad++ can find the word "inside" inside it and the whole data is decrypted in memory and thus in the memory dump file. I even didn't download any hacker tool, making dump files of running processes is part of Windows and the Task Manager, it's simply an option of the context menu of a process.
So while the whole data really is in its encrypted state on HDD in the EXE file itself, VFPs runtime does decrypt the EXE while running and thus embedded data also isn't safe from prying eyes, even not with VFPs internal encryption option used.
The code running was simply this:
Code:
On Shutdown Quit
Select * From includeddata INTO CURSOR crsLoadedData
Read Events
Is the query the vulnerability loading the data? Well, no, even if the data only is in the dump file because this cursor is the query result, how else would you make use of embebded data when not querying or using it in any way?
So finally: Embedding data inside an EXEcutable makes it harder to get at it, but it's not safe there. If you ever thought about that for safety of internal knowledge/meta data/license codes/passwords or anything else your code only needs to read: No, it's not safer than data put in source code or unencrypted extra DBF files.
Bye, Olaf.
PS: Just to make sure I also compiled an exe without the SELECT * FROM includeddata and the data still shows up in the dump file, so the main vulnerability is simply the decrypted state of everything in memory.

![[bigsmile] [bigsmile] [bigsmile]](/data/assets/smilies/bigsmile.gif)